What are Impersonation Tokens?
Ever wondered why you do not need to re-enter your password to access folders on your windows computer after you have logged in? The answer is Tokens. Tokens are given to you after login to prove you are authorised to access resources. They work the same as cookies for web applications. This means that just like cookies, if an attacker gets your tokens they can bypass authentication and impersonate you.
There are two types of tokens issued by windows.
- Delegation Token – Created upon login to a system.
- Impersonate Token – Used for none interactive type tasks such as using scripts that require authorisation, attaching network devices etc.
Accessing Tokens with Meterpreter
Meterpreter includes a module called “incognito”. To access the module run “load incognito” in your meterpreter shell.
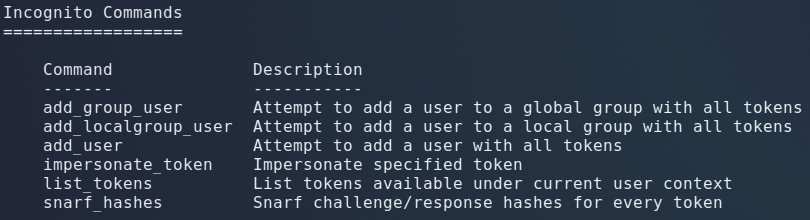
Listing available user tokens(logged in users) with list_tokens:

Dropping into a shell and confirming we are logged in as smarsh.

Impersonating Administrators Delegation Token

