What is Bloodhound?
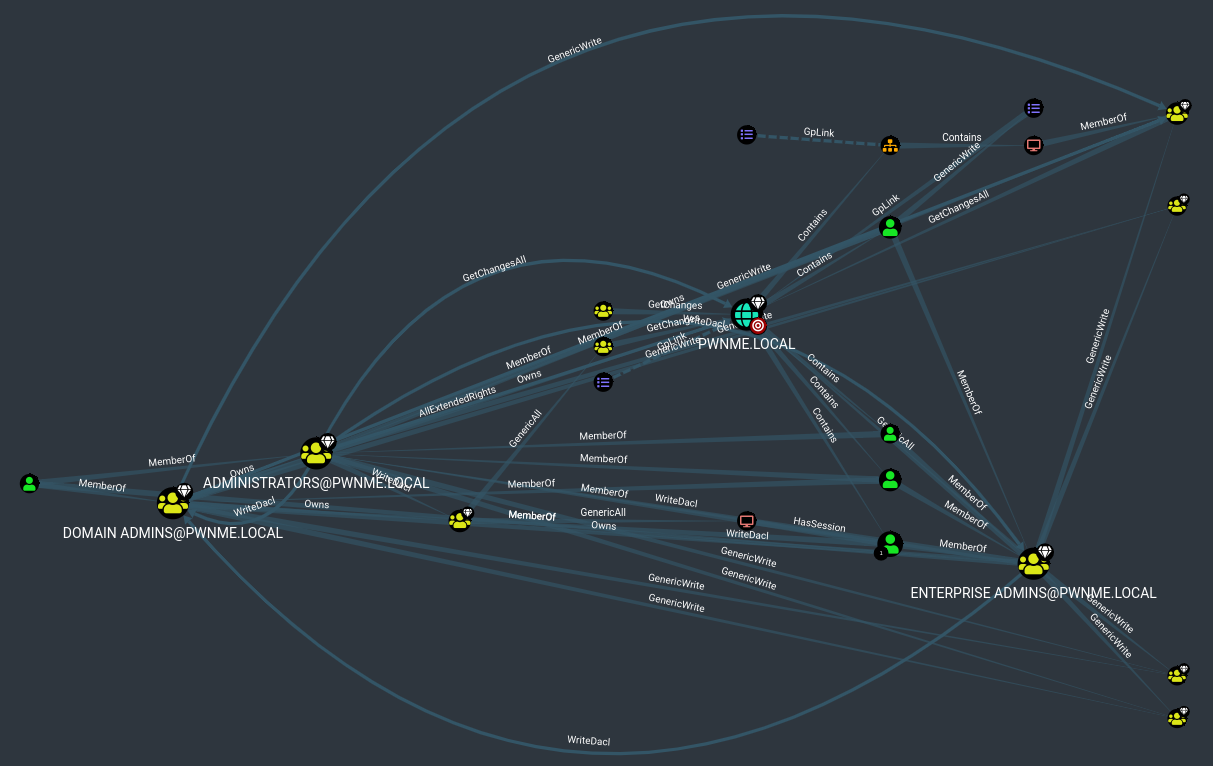
Bloodhound is a tool developed to visually graph complex relationships within Active Directory that would be extremely difficult to locate manually. Thus the tool is used by blue teams to secure and red teams for post compromise enumeration. The tool is extremely powerful as can be seen from the below screenshot:
Setting up Bloodhound
Bloodhound can be installed from the Kali repo:
apt install bloodhound
Once installed the neo4j server and database needs to be started:
neo4j console
Connect to the database and setup username and password with:
http://localhost:7474/
From console start bloodhound by just typing bloodhound.
Injesting data with a collector
Now that bloodhound has been setup we need data to feed it. To do this we copy a bloodhound injester to the windows machine which will perform enumeration and collection for us and output it to a file which we then transfer back to our machine and load it into bloodhound. As of writing there are 3 collectors that can be used:
https://github.com/BloodHoundAD/BloodHound/tree/master/Collectors
SharpHound.exe
SharpHound.ps1
AzureHound.ps1
I will use Sharphound.ps1 as most compromises will be done via shell. Transfer the ps1 file to the remote machine and run:
powershell -ep bypass
. .\SharpHound.ps1
Invoke-BloodHound -CollectionMethod All -Domain pwnme.local -zipFileName hound.zip
This will run a the collection and store it in hound.zip.
Graphing the collected data
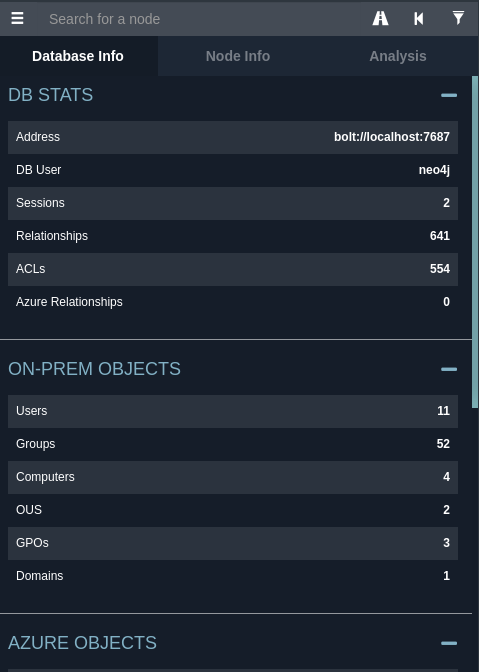
Back on your BloodHound instance login and upload the hound.zip file via the up arrow to the right of the screen. Once imported click the 3 lines at the top left of the window to view the Database info. This shows you the AD info and relationships etc.
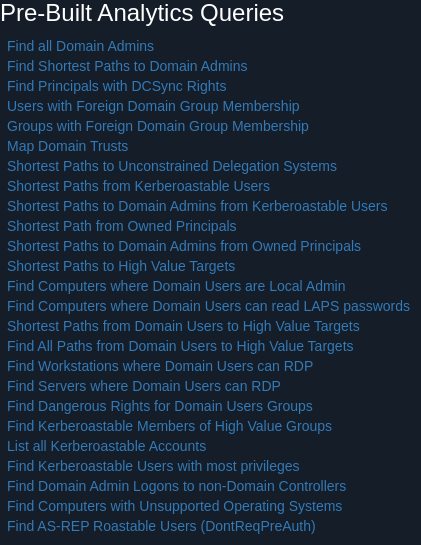
To Graph the data, go to the Analysis tab and choose what you would like to enumerate.
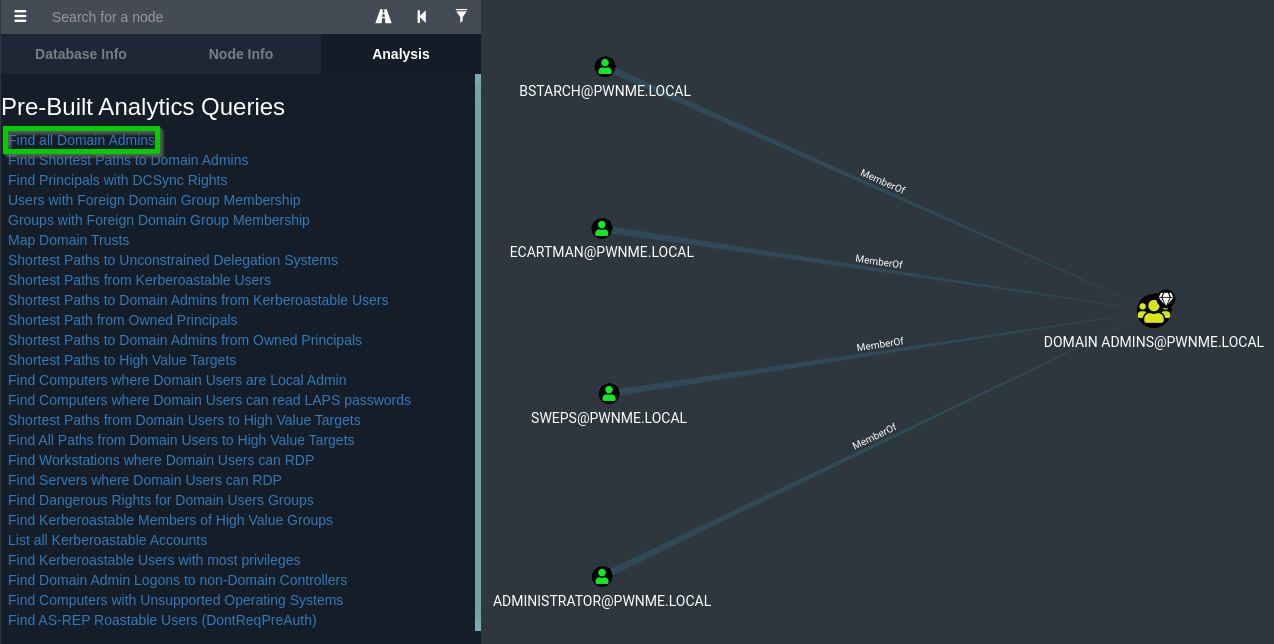
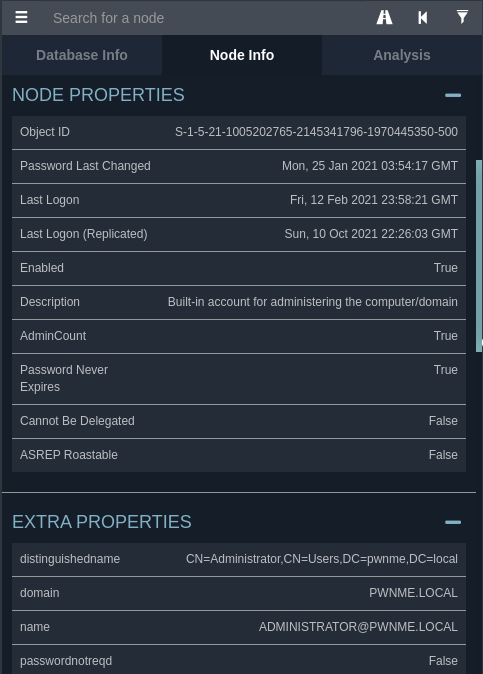
By clicking on a node you can bring up the properties of that node
Selecting “Find Shortest Paths to Domain Admins”. This shows the shortest route to get to Domain Administrator. We can see that ecartman, who is a domain administrator is logged into machine SOUTHPARK.PWNME.LOCAL so this would be a perfect target to maybe try passing a hash and using Token Impersonation to login to the Domain Controller etc.
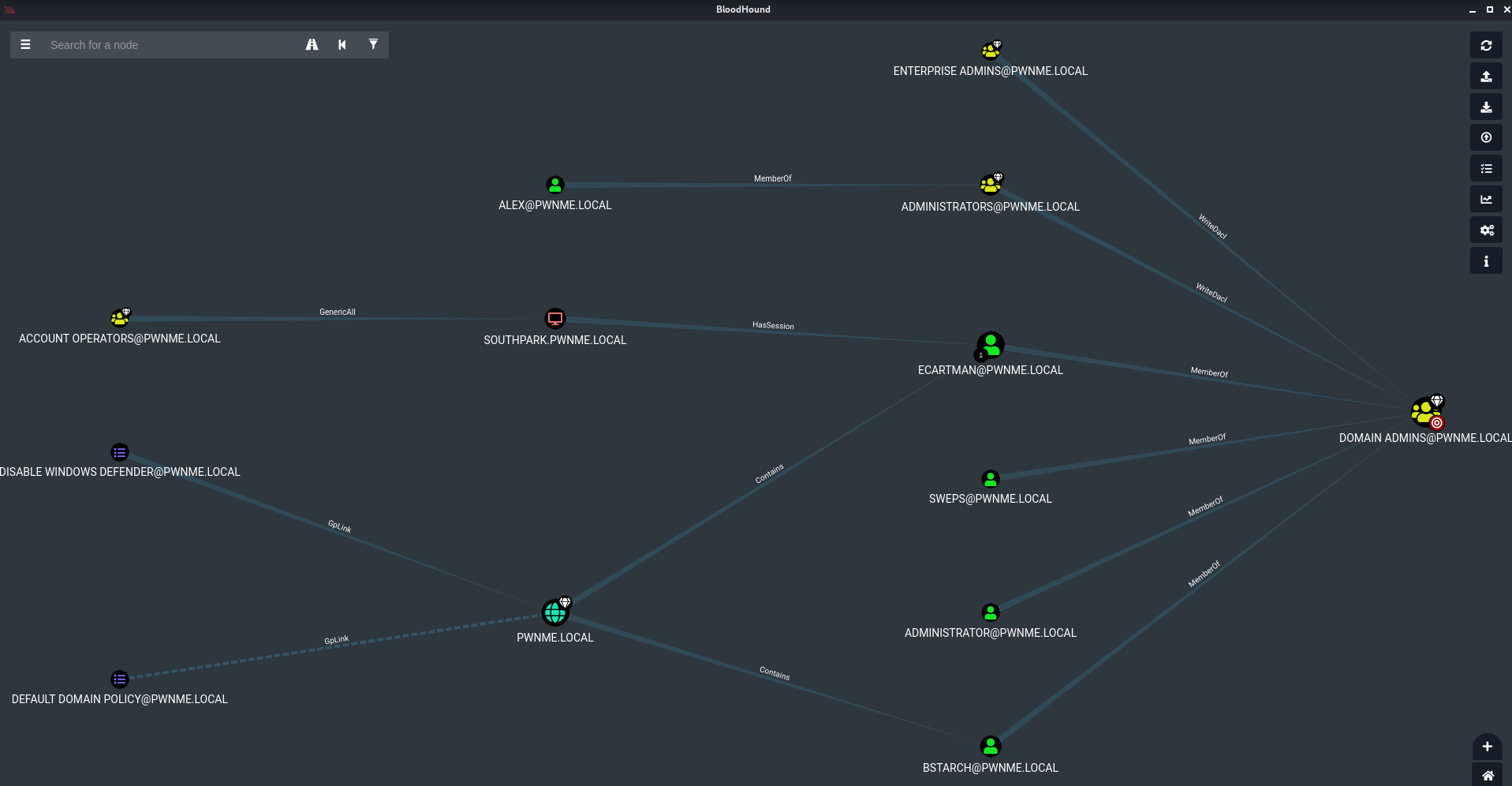
To further demonstrate the power of Blood hound, this is a result of selecting Shortest Paths to High Value Targets. This is a lab with less than 10 users and computers. Imagine a coorperate network with hundreds… This post has shown a very small fraction of what BloodHound is capable of.